Hacking Explained: URL Spoofing Trick
When a user loads an https link in Google Chrome, Mozilla Firefox, Microsoft Edge, or Internet Explorer it shows a nice green secure lock and protocol (https) in the url:
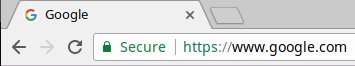
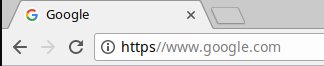
However when you load an http url it trims the protocol from the url bar:

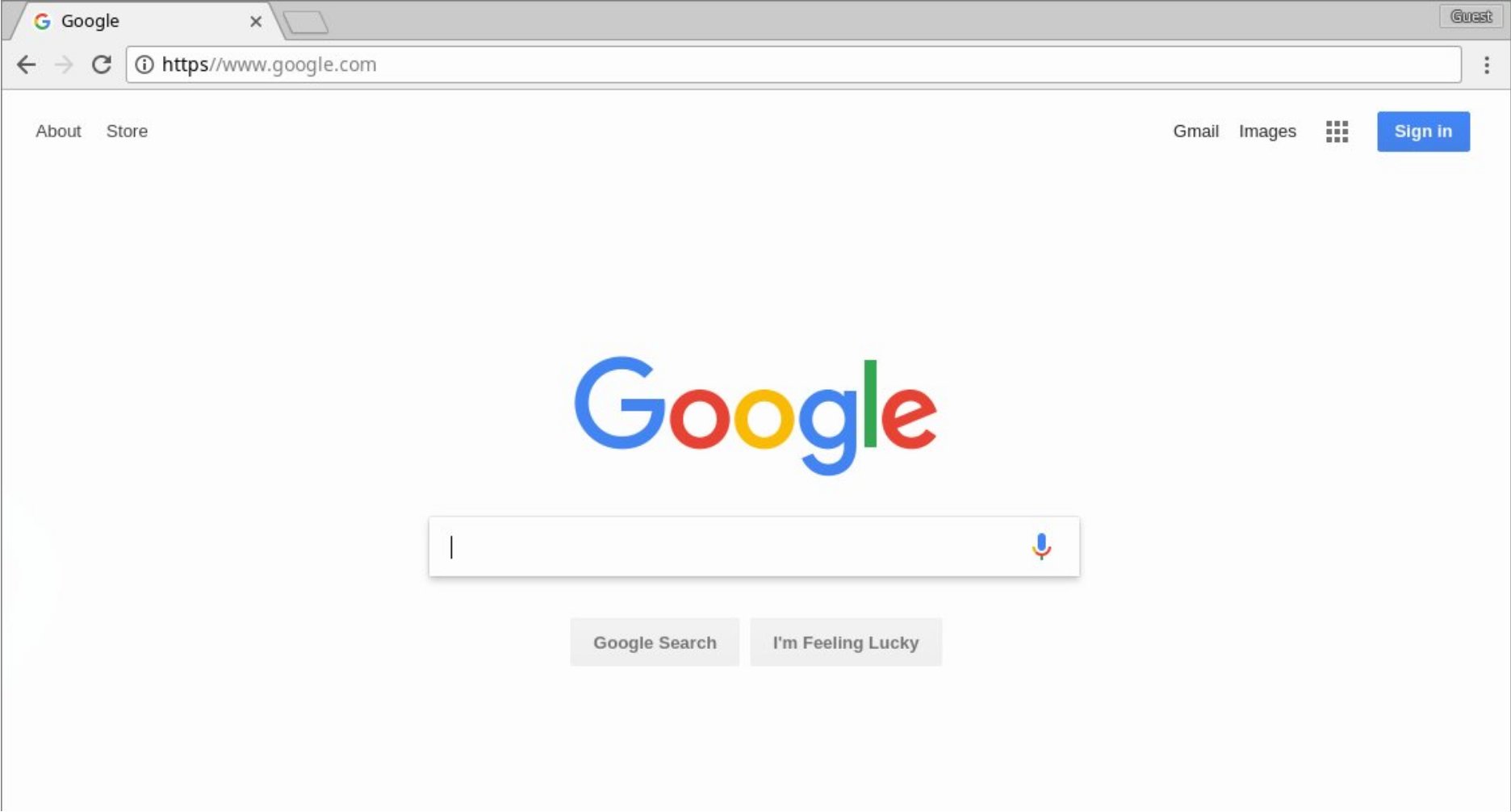
This opens up the opportunity for a subtle trick for url spoofing in Chrome. What if we use https as the domain and put the domain we’re spoofing in the path like this?
We can have the browser render pages that include https in the url bar and may appear legitimate to the less security-conscious (or just less conscious) user.
Check out my other articles describing ARP Spoofing and DNS Spoofing which demonstrate how one would be in a position to utilize this trick.
Here’s a demonstration of how this trick can be used to generate a pretty convincing victim scenario:
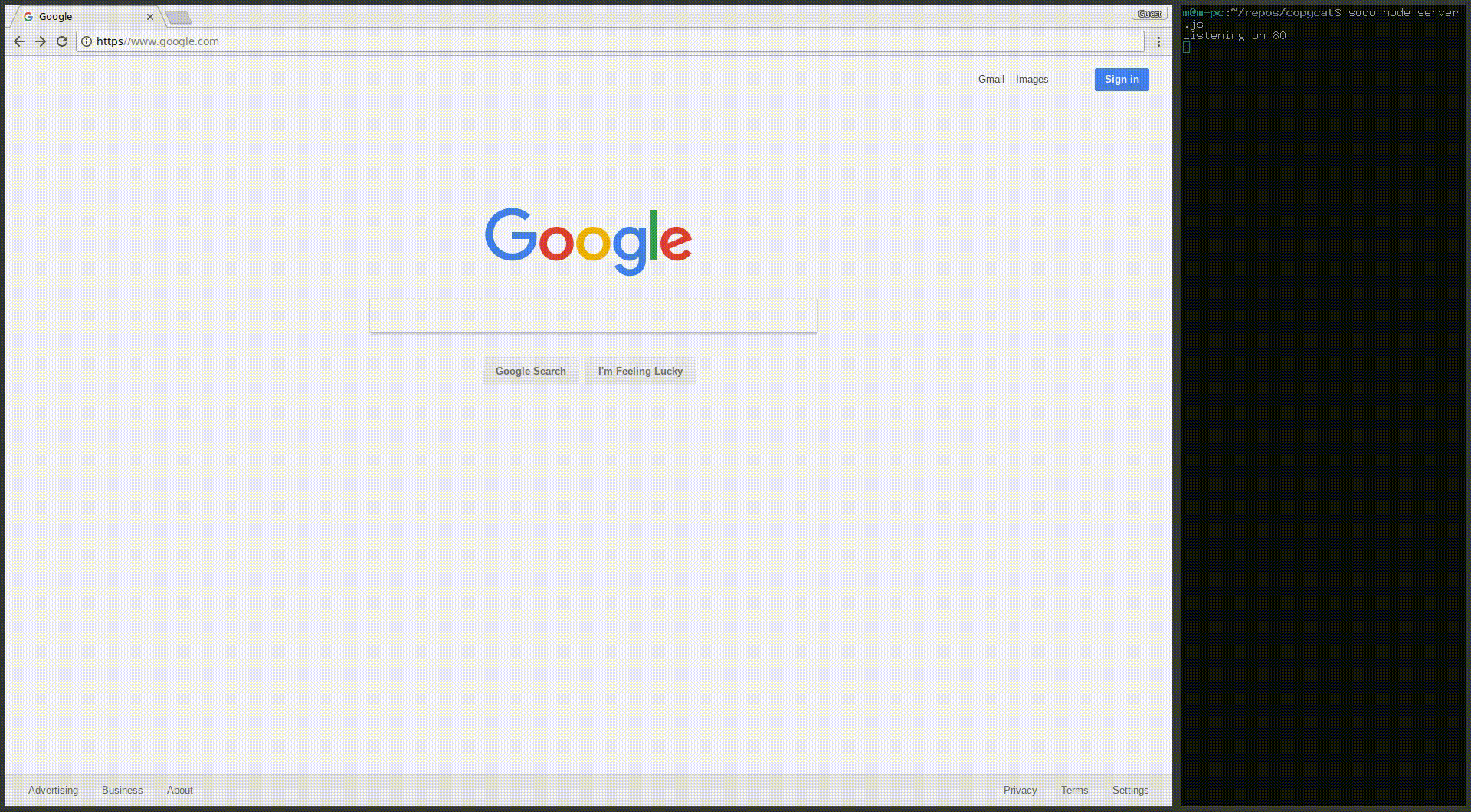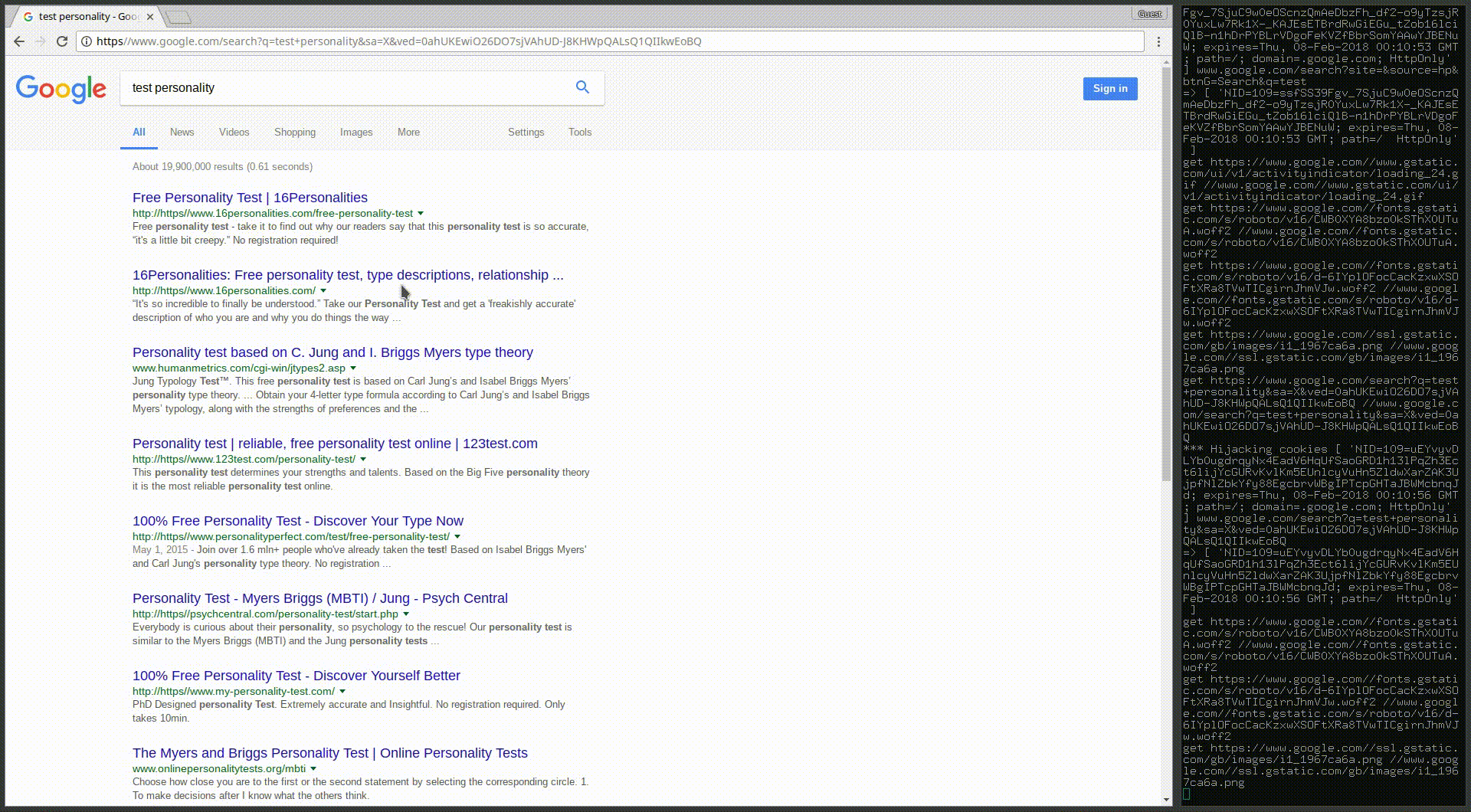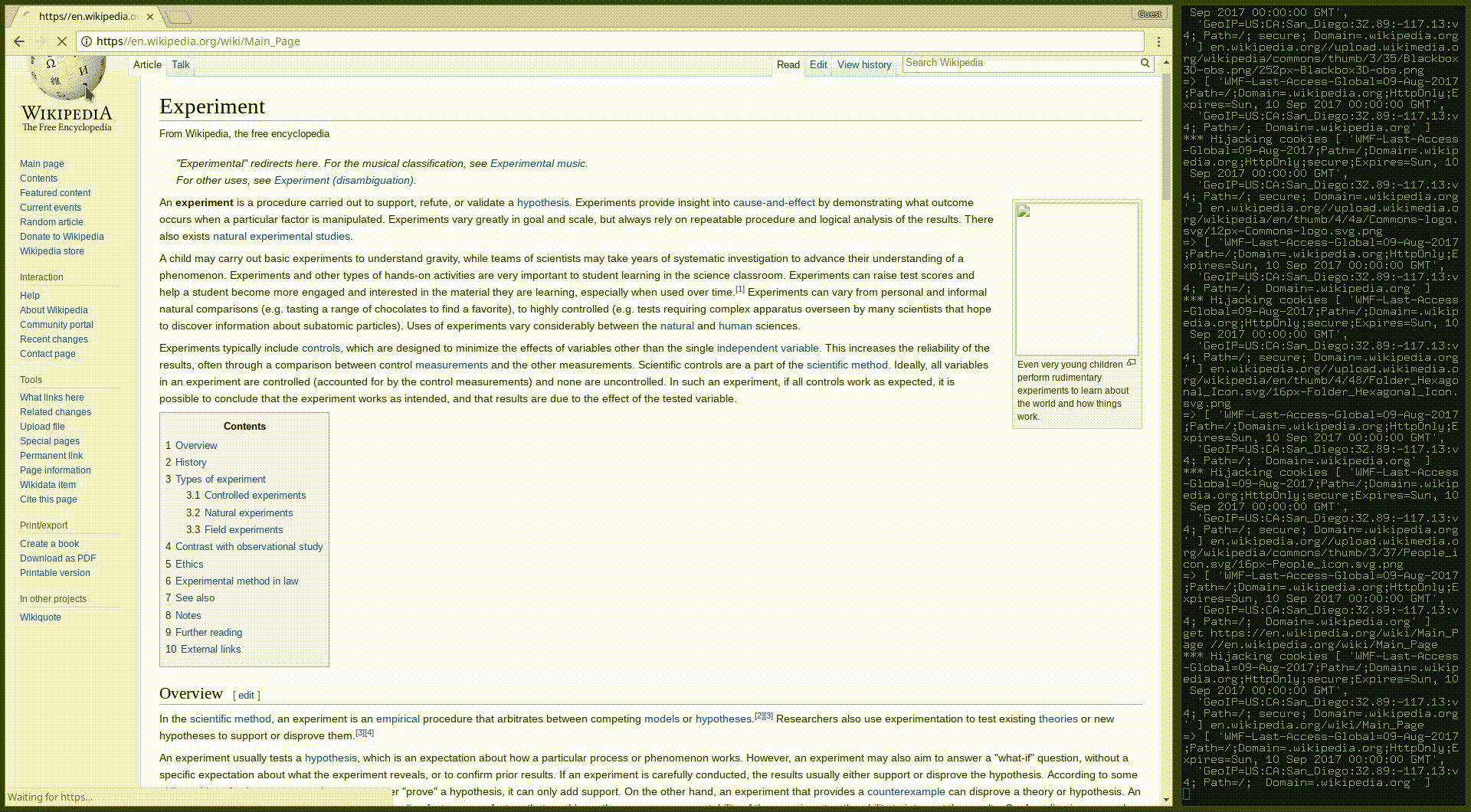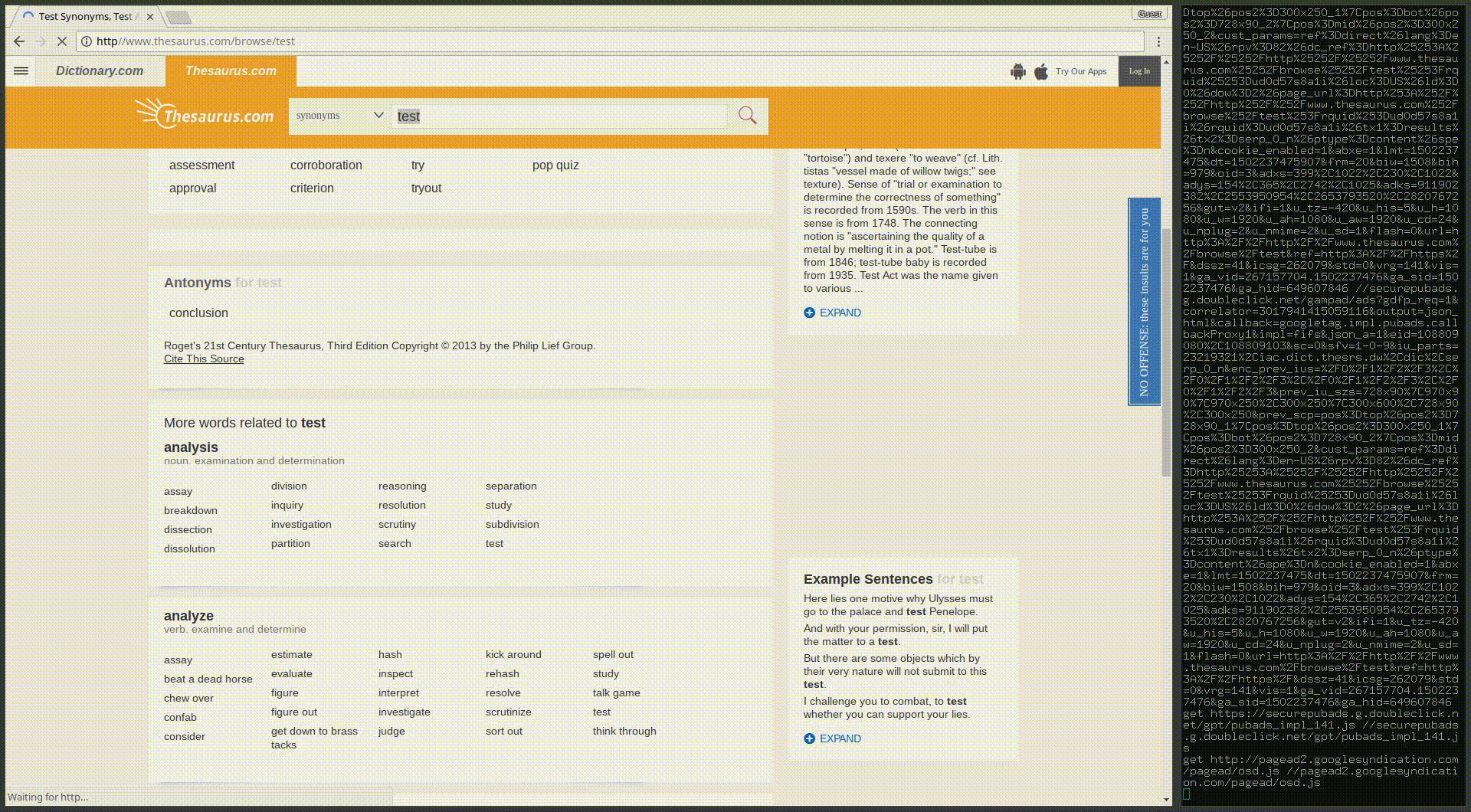
I’ve utilized this trick in the development version of my universal man-in-the-middle tool CopyCat. Once that’s a little more stable I’ll be releasing the latest more powerful version as well as a full writeup on how it works.
I haven’t thought of any legitimate reasons for these web browsers not to show the protocol in the url bar as they do with https. But if they have good reasons to do so, they should be weighed against this potential attack.

© 2025 Viam Technologies
