Hacking Explained: ARP Spoofing
The Address Resolution Protocol (ARP) is generally used to map unique MAC addresses to their corresponding IP addresses on a network. For example, let’s consider the following network configuration:
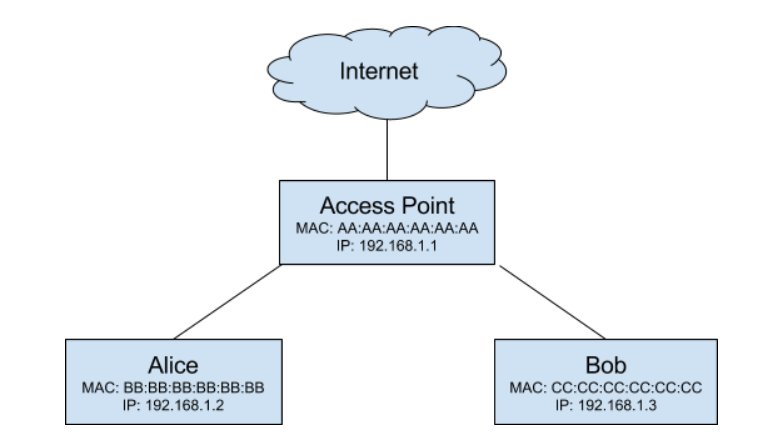
Each of these devices has a unique hardware MAC address (typically assigned by the manufacturer, but modifiable with software) which is used at one layer of the network, and an ideally unique IP address which is used at another layer. When Client A wants to send a packet to Client B, they need to include Client B's MAC address. If Client A does not have Client B's MAC address they broadcast a request to the entire network asking "who has 192.168.1.3" (Client B's IP address). If Client B receives this request they respond "I am 192.168.1.3" which includes their MAC address (CC:CC:CC:CC:CC:CC). Client A then stores this mapping of Client B's MAC address (CC:CC:CC:CC:CC:CC) and their IP address (192.168.1.3) locally in an ARP Table.
Devices will also automatically update their ARP table whenever an ARP reply ("I am xx.xx.xx.xx") is received regardless of whether or not the client initiated the ARP request. ARP does not define any way of validating or authenticating these requests/responses and this allows an attacker to manipulate client ARP tables at will.
In our example above, an Attacker and a Victim have their clients configured to use the Access Point's IP address (192.168.1.1) as their default gateway to the Internet. Using our knowledge of ARP, the Attacker can modify the Victim's ARP table to use the Attacker's MAC address for the IP address of the default gateway by simply sending an ARP reply to the Victim which says "I am 192.168.1.1". The Victim's device will then update it's ARP table and use this new mapping for subsequent requests as represented by the following image:
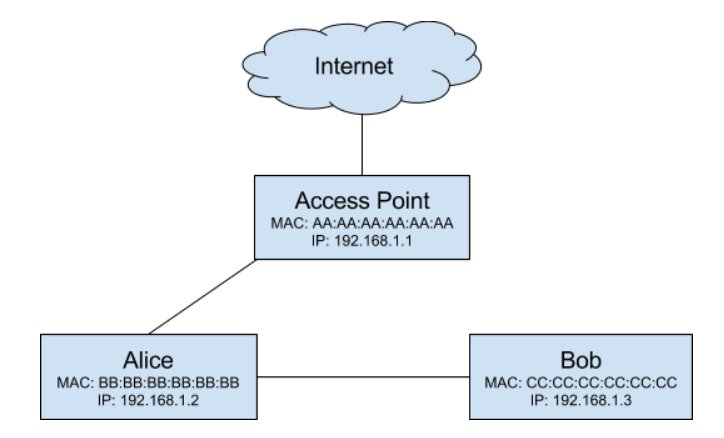
The Attacker could then configure their client to forward all of the traffic from the Victim to the Access Point, allowing the Victim to still have access to the Internet, while they act as a man in the middle. Keep in mind however, if the Victim is encrypting their traffic with the other devices they're communicating with the Attacker will only see the encrypted traffic. This is why using websites with HTTPS is incredibly important.
I began developing CopyCat as a proof of concept tool for attackers to circumvent the security provided by HTTPS and see/modify the traffic, and allow victims to continue to use the services provided by HTTPS web servers. Check out my articles on using DNS Spoofing and my URL Spoofing Trick for Chrome to see some examples of things you can do with ARP Spoofing!

© 2025 Viam Technologies
